How To Crack Ransomware Virus Decryption Key Files Removal For Free?
Ransomware Crack is a particularly aggressive form of malware that typically captures a victim’s data or device and holds them. Ransomware Crack victims can now recover files for free researchers looked into this latest form of ransomware and found easy ways to crack it. Victims of a new form of ransomware virus introduced just a few weeks ago can now recover their encrypted files without having pay to ransom attackers.
What Is A Ransomware Crack Virus?
Once a rare and obscure malware, ransomware now has a huge impact on almost everyone. This number of ransomware attacks has increased by 150% between 2019 and 2020. Despite accounting for only around 15% of all cyberattacks, ransomware is also among the most expensive, costing businesses nearly $2 million. dollars to repair each attack.
What Is A Ransomware Virus Attack?
At its core, ransomware is just another form of malware. It is a malicious program designed to infect and disrupt the normal functioning of a computer system.
However, two key characteristics of ransomware set it apart from most other forms of malware:
- Instead of stealing data, ransomware is designed to prevent access to it.
- Instead of selling or using your stolen data, cybercriminals try to force you to pay a ransom in order to regain access to your data.
Where malware has traditionally been about stealing data, ransomware does ransomware. Otherwise, the methods used by cybercriminals to infect computers with ransomware are the same as with any other malware. Hackers can also download ransomware into the system if they hack the system with brute force or use stolen login credentials.
How Does Ransomware Crack work?
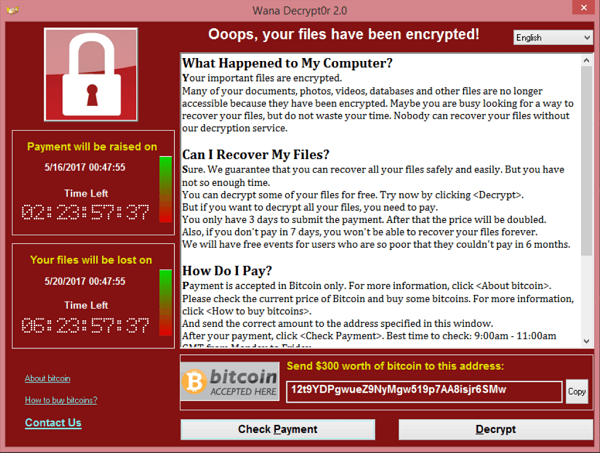
RansomWarrior appears to be the work of hackers working from all over the world, judging by the inclusion of “Have a nice day with love” in the ransom note. The file blocking malware targets Microsoft Windows users and is delivered to victims via an executable called “A Big Present.exe” that, when run, encrypts files with the.THBEC extension.
Victims receive a ransom note and are instructed to visit a dark web address to pay an unspecified ransom in bitcoin cryptocurrency. The attackers offer the victims to decrypt the two files for free, but the note also reminds the victims that if they don’t pay the ransom, they won’t get their files back. Victims are also intimidated not to report the attack to the police, and the attackers are told that law enforcement “can’t help you.”
Everything You Need To Know About Ransomware Crack?
Everything you need to know about one of the biggest threats on the Internet, Check Point researchers analyzed RansomWarrior and found it to be the work of seemingly inexperienced attackers who were able to recover the decryption keys for the malware. Check Point was successful due to the weak encryption used by the ransomware crack, which is a stream cipher using a randomly generated key from 1000 keys hard-coded in the RansomWarrior binary.
Because the key index is stored locally on the victim’s computer to provide the means to unlock files, the researchers were able to create a decryption tool for anyone infected with RansomWarrior. While many cybercriminals use cryptocurrency mining malware as a more subtle and less risky way to get bitcoin and other cryptocurrencies, ransomware remains a major cyber threat. Instead of deploying massive spam campaigns to infect as many users as possible, the most successful ransomware crack campaigns have developed a new tactic.
Types of Ransomware Crack:
Ransomware has been around since the 1980s, but many attacks today use ransomware based on the more modern Cryptolocker Trojan. Ransomware that encrypts files is becoming more common. In addition, many hackers are now using double encryption techniques that use two types of malware to lock files.
According to Malwarebytes, there are several categories of ransomware that you may still encounter:
Ransomware Encryption:
If ransomware gets into your computer, it’s most likely some form of encryption. Ransomware encryption is rapidly becoming the most common type due to the high ROI for cybercriminals who use it and the difficulty of cracking the encryption or removing malware. It’s a favorite among hackers because most antivirus tools simply don’t work to prevent this and can’t effectively remove the encryption after an infection.
Ransomware encryption will completely encrypt the files on your system and prevent you from accessing them until you pay the ransom, usually in the form of bitcoins. Some of these programs are also time sensitive and will start deleting files until the ransom is paid, adding to the sense of urgency to pay.
About this type of ransomware, Adam Kujava, director of Malwarebytes Labs, had the following to say: “When you are infected, it is already too late. Game over.” Online backup can be of great help in recovering encrypted files. Most online backup services include versioning so you can access previous versions of files rather than encrypted versions.
Scareware:
Scareware is malicious software that tries to convince you that you have a computer virus that needs to be removed immediately. It will then try to force you to remove the virus by purchasing a suspicious and usually bogus malware or virus removal program. Scary programs are very rare these days, but some of these viruses still exist in the wild. Many are aimed at cell phones.
Scarecrow virus usually does not encrypt files, although it may try to block access to certain programs (such as antivirus and uninstallers). However, scary programs are the easiest to eliminate. In fact, in most cases, you can remove malware using standard virus removal programs or other methods without even entering Safe Mode (although this may still be necessary or recommended).
Screen lock:
Screen locks will display a warning screen that restricts your ability to access computer features and files. They may be installed on your computer or they may exist in your web browser. They usually come with a message that they represent a law enforcement organization and try to convince you that you will face serious legal consequences if you do not pay the fine immediately.
This type of virus can be installed in a variety of ways, including visiting hacked websites or clicking and downloading an infected file contained in an email. When installing directly on a computer, a hard reboot may be required to regain access to the system. However, you may also find that you are still welcomed by a message on the lock screen even when the operating system boots up again.
Screen locks tend to block access to menus and other system settings, but they don’t always block access to your files. Some of the main malware attack methods prevent you from easily accessing virus removal software and sometimes can even prevent you from restarting your computer from the user interface.
How To Prevent Ransomware Crack?
Decrypting files encrypted with ransomware is incredibly difficult. Unless you pay the ransom and receive the decryption key from the attacker, decrypting the ransomware is next to impossible. Most ransomware these days uses AES or RSA encryption methods which are functionally impossible to break through brute force.
In comparison, the US government also uses AES encryption standards. Information on how to create such encryption is widely known, as is the difficulty of breaking it. The best way to fight ransomware is to eliminate the risk of infection. The significant cost and the difficulty of decrypting without paying a ransom means that prevention is your best strategy. You can protect yourself against ransomware by fixing weaknesses in your system, network, or organization and changing the behavior that exposes you or your business to ransomware attacks.
Best practices to prevent ransomware
- Invest in reliable data backup. It’s hard to underestimate. Backing up your data is the best thing you can do. Even if you are attacked by ransomware, effective and consistent data backup means your data will be safe no matter what type of ransomware attacks you.
- Invest in effective antivirus software. In this case, you not only need malware or virus removal tools, but also software that will actively monitor and warn you of threats, including those present in web browsers. Thus, you will receive notifications of suspicious links or be redirected from malicious websites where ransomware may be hosted.
- Never click on suspicious email links. Most ransomware is distributed via email. When you make a habit of never clicking on suspicious links, you greatly reduce your risk of downloading ransomware and other viruses.
Protect computers connected to the network. Some ransomware works by actively scanning networks and gaining access to all connected computers that allow remote access. Make sure remote access is disabled on all computers on your network or use strict security measures to prevent easy access. - Keep the software up to date. Updates for Windows and other operating systems and applications often fix known security vulnerabilities. Keeping up to date can help reduce the risk of exposure to malware, including ransomware.
- Invest in ransomware protection. Especially useful for small businesses and network administrators to monitor and respond to emerging threats. Many antivirus tools now include anti-ransomware solutions that detect the use of behavioral analysis to prevent ransomware from running before it begins the encryption process.
How to Install or Activate Patch Ransomware Decryption with Crack?
- First, download the Patch Ransomware Decryption Crack file from the specified link.
- After downloading, extract the archive Crack Installer files using WinRAR/WinZip or any other software.
- Open the extracted folder, Read the readme file.
- Run the setup.exe and keep clicking until you are prompted to specify a location on the disk where you want to install the software.
- While the installation process is complete, Do not run the software immediately.
- On completing the installation process, run the patch file and click the Next button, copy the keygen file and paste that file to the folder where you have installed the software.
- It may take a few seconds and will crack.
- A shortcut to the program will appear on your desktop when it’s completed.
- Enjoy you are done, and reboot your system for high performance.